|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
Increased Fog and Akira Ransomware Activity Linked to SonicWall SSL VPN
|
|
|
|
Throughout October, there has been a significant increase in Fog and Akira ransomware intrusions targeting SonicWall SSL VPN users across various industries. The attacks appear opportunistic rather than targeting specific sectors. All affected devices lacked patches for CVE-2024-40766.
Initial access involved VPN logins from VPS hosting IPs, with rapid progression to data encryption and exfiltration, often within hours. Shared infrastructure was observed across multiple intrusions. Defenders are advised to prioritize firmware updates, monitor for suspicious VPN logins, maintain secure offsite backups, and watch for post-compromise activities on endpoints.
|
|
|
|
LevelBlue Labs latest blog: Ngioproxy
|
In August 2018, Check Point published a report and deep analysis on a new multifunctional proxy server botnet named Ngioweb. The proxy service was being loaded by the banking malware family Ramnit. In their report, Check Point reported that the first sample was observed in the second half of 2017.
LevelBlue Labs has recently identified systems infected with Ngioweb trojan being sold as residential proxy servers in the Nsock webpage. In almost all cases, systems targeted were IoT (Internet of Things) devices that had known published vulnerabilities, some with public proof of concepts available. See LevelBlue Labs’ most recent blog to learn more.
|
|
|
|
Silent Threat: Red Team Tool EDRSilencer Disrupting Endpoint Security Solutions
|
EDRSilencer, a red team tool designed to interfere with endpoint detection and response (EDR) solutions, has been discovered being abused by threat actors. It leverages the Windows Filtering Platform to block EDR traffic, concealing malicious activity.
The tool dynamically identifies running EDR processes and creates filters to block their outbound communication, preventing telemetry and alerts from reaching management consoles. During testing, it effectively disrupted various EDR products, including those not in its hardcoded list.
This tool represents a significant shift in tactics, enhancing the stealth of malicious activities and increasing the potential for successful attacks. Organizations must adapt their security posture to counteract these sophisticated evasion techniques.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
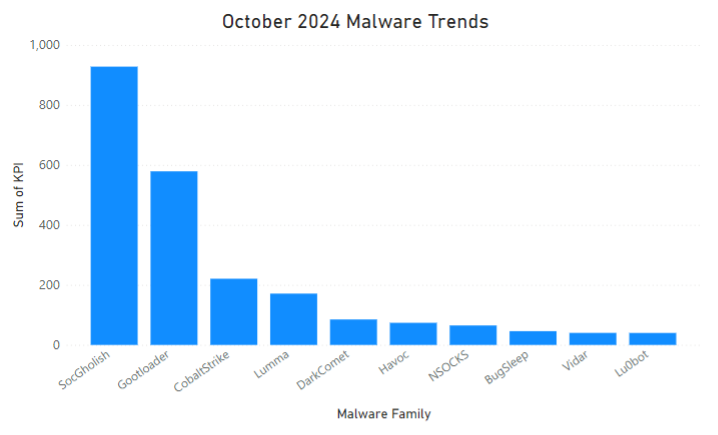
The team has identified the following malware/threat actors as the most active during the month of October. October’s malware trends continue to be very similar to previous months, with a main relevant inclusion:
|
- BugSleep: This remote access trojan, initially reported in early June by multiple security researchers and sometimes referred to as MuddyRot, allows access to a reverse shell for threat actors as well as file input and output capabilities. Since their initial report it has become more prevalent after initial access to maintain C2 and provide an avenue for exfiltration.
|
|
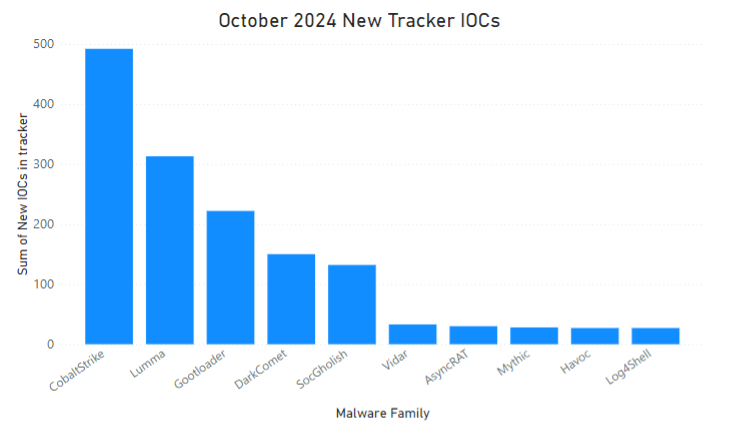
The LevelBlue trackers have identified over 1600 new IOCs for the different families it tracks. The busiest trackers during the month of October have been:
|
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In October, LevelBlue Labs added or updated 52 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- New rules related to System Compromise for EDRSilencer and attempts to block EDR traffic locally on endpoints.
- Improvements to Fortinet detections to provide coverage for fgfm daemon vulnerability.
- Several rules for phishing detections in O365 and Proofpoint.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily.
LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise, IoCs, that are useful to members.
In October, 139 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|