|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
Last Tuesday April 29th, LevelBlue Labs made a significant impact at the RSA Conference in San Francisco, with team members Santiago Cortes and Fernando Martinez leading a session on the usage of residential proxies by cybercriminals.
Their presentation, titled "Residential Proxies — Why Is My Cell Phone for Sale on the Dark Web?" delved into how these proxies are used to mask malicious activities and bypass security measures. By examining recent campaigns such as NSOCKS and ProxyNation, Santiago and Fernando provided attendees with a comprehensive understanding of the sophisticated techniques employed to hijack devices and expand proxy networks.
The insights shared by the LevelBlue Labs team underscored the importance of staying ahead in the ever-changing landscape of cybersecurity, and how we might be part of these botnets through the use of free applications. This session was a testament to LevelBlue Labs' commitment to advancing cybersecurity knowledge and protecting digital environments from emerging threats.
|
|
|
|
ClickFix Becomes Viral
|
In recent months, the ClickFix social engineering technique has gained significant traction among cybercriminals and state-sponsored actors alike.
First observed in March 2024 by the initial access broker TA571, this technique has evolved in just one year into a favored method for deploying malware. This technique manipulates users into executing malicious commands by either automatically or manually copying and pasting a malicious command into their terminal or Run dialog, under the guise of routine actions or resolution to non-existing issues.
As ClickFix continues to proliferate, understanding its mechanics and the threats it poses is crucial for bolstering cybersecurity defenses. In the last few weeks, it has been observed in various high-profile campaigns:
|
- Lazarus, a North Korean state-sponsored threat actor, has launched a new campaign called ClickFake Interview targeting cryptocurrency job seekers as reported by Sekoia.
- This campaign uses fake job interview websites to deploy the GolangGhost backdoor on Windows and macOS systems.
- The campaign primarily targets centralized finance (CeFi) entities, aligning with Lazarus' focus on cryptocurrency-related targets.
- Notable changes include targeting non-technical roles and using ReactJS-based websites for the fake interviews. The malware gains Initial Access through a ClickFix bait and provides remote control and data theft capabilities, including browser information exfiltration
|
- The Interlock ransomware group, active since September 2024, has shown adaptability and innovation in its tactics despite a relatively low victim count.
- Sekoia has reported the group has been employing fake browser updates and the ClickFix technique for initial access, followed by a multi-stage attack chain involving PowerShell backdoors, credential stealers, and a custom Remote Access Trojan.
- The group targets various sectors across North America and Europe, conducting Big Game Hunting and double extortion campaigns.
- Interlock has been observed improving their tools, including modifying their ransom notes to emphasize legal repercussions.
|
- A phishing campaign targeting organizations in the hospitality industry was identified by Microsoft in March.
- They were impersonating Booking.com and using the ClickFix social engineering technique to deliver multiple credential-stealing malware.
- The campaign, tracked as Storm-1865, targets individuals likely to work with Booking.com in North America, Oceania, Asia, and Europe.
- The attack uses fake emails and webpages to trick users into executing malicious commands, leading to the download of various malware families including XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT.
- The campaign aims to steal financial data and credentials for fraudulent use, showing an evolution in the threat actor's tactics to bypass conventional security measures.
|
|
|
|
SonicWall SMA Credential Access Campaign
|
|
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
LevelBlue Labs has created or updated the following Adversary Trackers to automatically identify and detect malicious infrastructure:
|
|
|
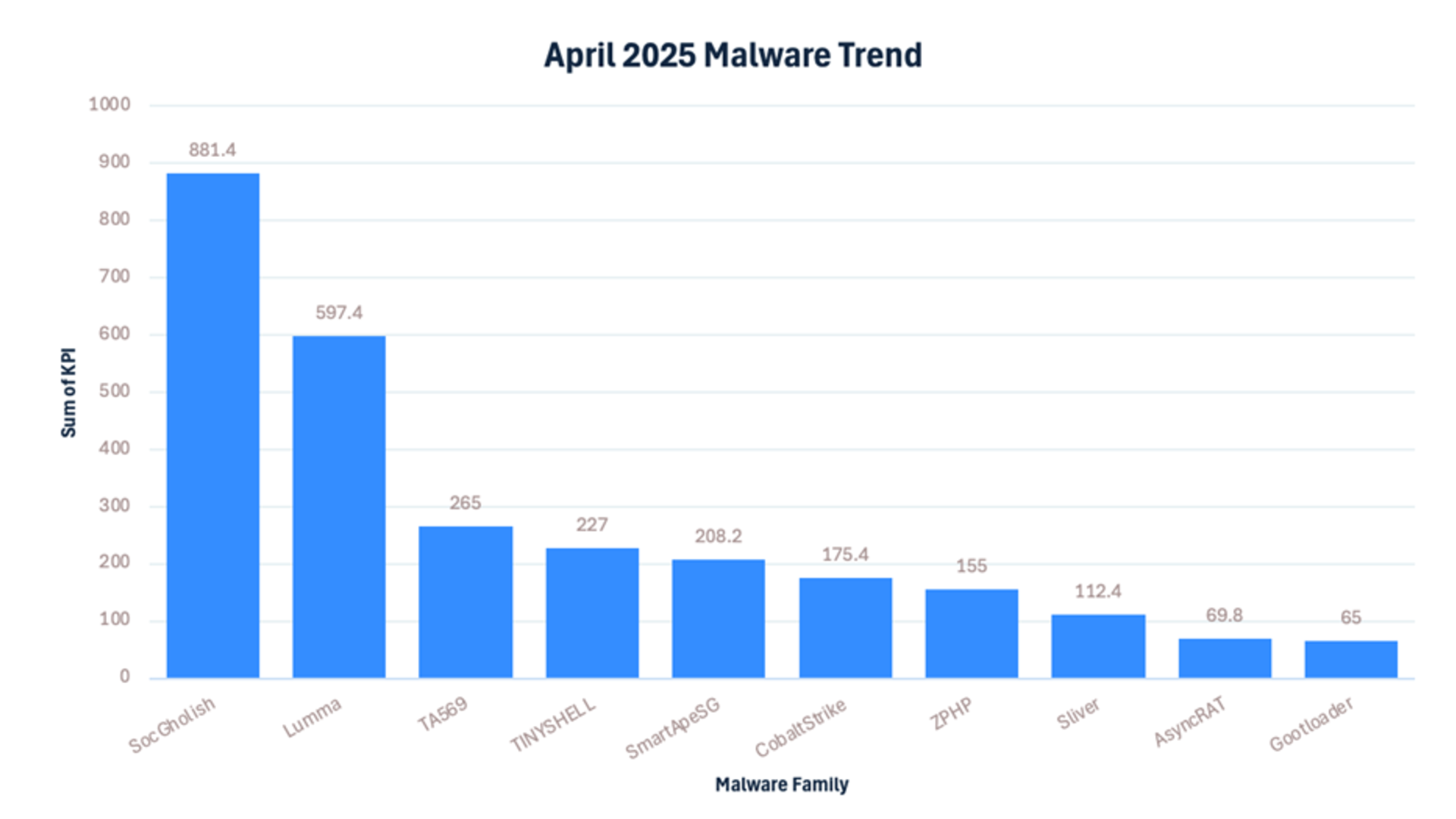
The team has identified the following malware/threat actors as the most active during the month of April.
|
- TA569: The threat actor, serving as initial access broker and pay-per-install service, continues to use fake update-themed lures like SocGholish and Gholoader to infect victims for malware installation and follow-on ransomware attacks.
|
|
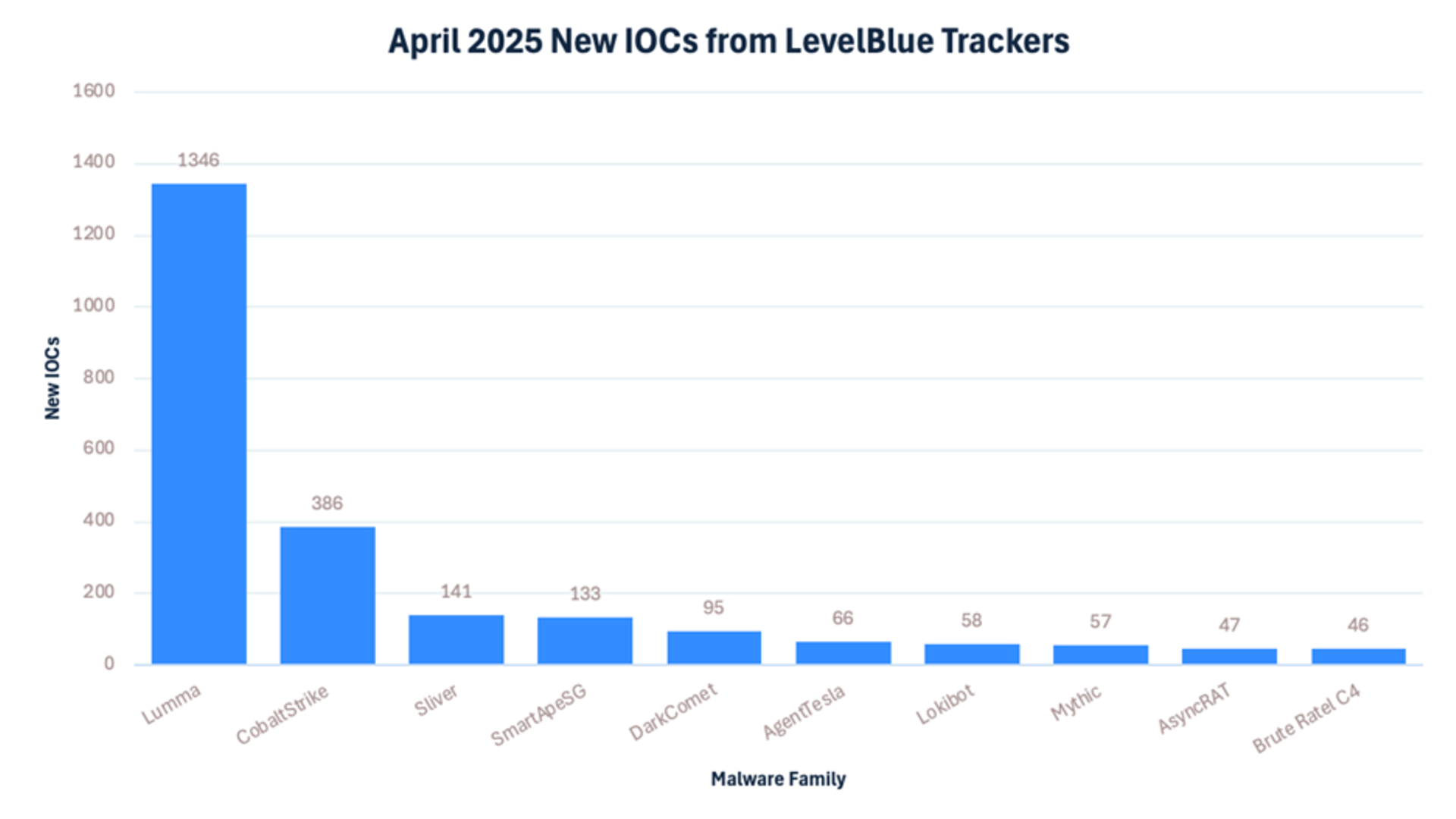
The LevelBlue trackers have identified over 2700 new IOCs for the different families it tracks. The busiest trackers during the month of April have been:
|
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In April, LevelBlue Labs added or updated 138 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- New Akamai ruleset with 9 new detections for its SIEM plugin.
- Updated several Windows generic rules to detect the AbyssWorker driver, a malicious driver used with the MEDUSA ransomware attack-chain to disable anti-malware tools.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily.
LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise (IOCs) that are useful to members.
In April, 116 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|