|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
|
Latest Threat Intelligence News
|
|
|
|
|
|
|
BlackBasta Internal Chats Leaked
|
|
|
|
The leak comes three years after a very similar case when one of the Conti operators leaked Conti's internal communication for a year timespan after the group announced their "full support" for Russia in the Ukraine war.
|
|
|
|
Sandworm APT Targets Cracked Windows Users in Ukraine
|
Analysts have reported that Sandworm (APT44), a Russian threat actor, is actively attacking Ukrainian Windows users. Sandworm leverages pirated Microsoft Key Management Service (KMS) activators and fake Windows updates to deliver a new version of BACKORDER, a loader previously associated with the group. BACKORDER ultimately deploys Dark Crystal RAT (DcRAT), enabling attackers to exfiltrate sensitive data and conduct cyber espionage.
Ukraine’s heavy reliance on cracked software, including within government institutions, creates a major attack surface. It is not the first time Ukraine companies have been hacked with malware bundled with cracked software.
ElectricIQ claimed the attribution is backed by the recurring use of ProtonMail accounts in WHOIS records, overlapping infrastructure, and consistent Tactics, Techniques and Procedures (TTPs). Additionally, the reuse of BACKORDER, DcRAT, and TOR network mechanisms, along with debug symbols referencing a Russian-language build environment, further reinforce confidence in Sandworm’s involvement.
|
|
|
|
GhostSocks and Lumma, Partners in Crime
|
Infrawatch has released an analysis on GhostSocks, a Golang-based SOCKS5 backconnect proxy malware. The report analyzes GhostSocks' integration with LummaC2 and its command-and-control infrastructure. The integration of the proxy with Lumma allows threat actors to maximize the monetization obtained from infected victims, and there are substantial discounts in GhostSocks for holders of a Lumma license.
The alliance between infostealers and proxyware improves performance while luring users through discounts, which can only lead to a double threat to residential users.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
The LevelBlue Labs team created or updated the following Adversary Trackers to automatically identify and detect malicious infrastructure:
|
- SmartApeSG (ZPHP)
- AdLoad
- Sneaky2FA
- Lumma Stealer
|
The team has identified the following malware/threat actors as the most active during the month of February. This month’s hotspot doesn’t show up in the top 10 malware trends, but it does appear in the tracker section::
|
- SmartApeSG: Also known as ZPHP, is a is a threat actor using fake browser updates in their social engineering attacks to distribute Netsupport RAT. Similar to SocGholish, these updates are distributed through injected scripts in compromised websites, making it harder to alert on the first stage of the infection process. The name was assigned after its preference for SmartApe ASN to host their infrastructure.
|
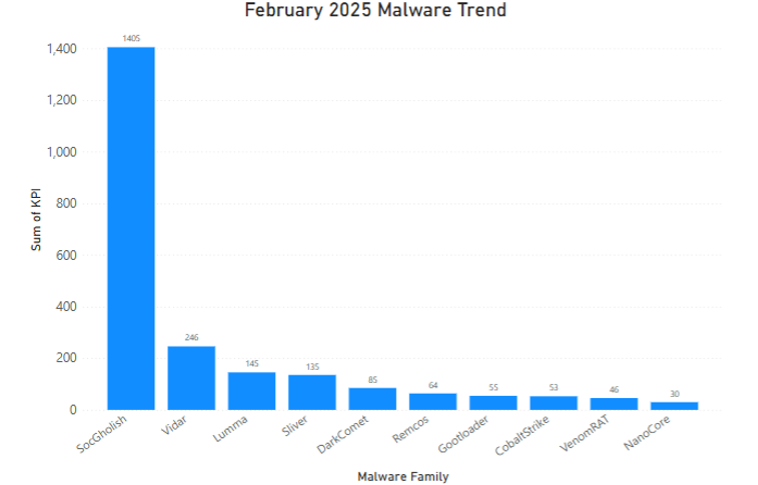
|
The LevelBlue trackers have identified over 1400 new IOCs for the different families it tracks. The busiest trackers during the month of February have been:
|
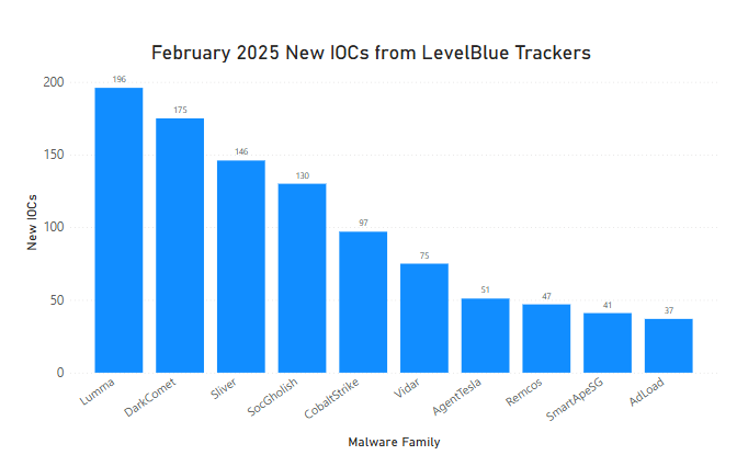
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In February, LevelBlue Labs added or updated 26 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- New rules related phishing in Avanan Email Security and O365.
- Improvements to Fortinet detections to provide coverage for web attacks and Windows exploits.
- Several rules for Pulse Connect Secure to identify Brute Force attempts.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily. LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more.
You can go here to find out more about the new pulses or to sign up to be part of the community.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise, IoCs, that are useful to members.
In February, 111 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|