|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
Scattered Spider Targets Fashion Retail
|
|
|
|
Scattered Spider, an English-speaking crime gang, have been targeting fashion retailers out of the UK, France, and the US. Most recently, retailers Marks and Spencer and Harrods out of the U.K. show signs that indicate Scattered Spider breaches. At the end of May, Victoria’s Secret had to take down their website for over 12 hours after they confirmed a breach.
Silent Push published a threat report on the group at the end of April detailing their tactics, delivery methodologies, and tooling. In their most recent campaigns, Scattered Spider has been deploying DragonForce ransomware once full compromise is achieved. Their intrusion methods involve heavy social engineering and vishing of senior individuals, and spoofing identities to recover credentials through support desks.
|
|
|
|
China-Nexus Nation State Actors Exploit SAP NetWeaver
|
Chinese state-sponsored Advanced Persistent Threat (APT) groups are exploiting a vulnerability in SAP NetWeaver Visual Composer to target critical infrastructure networks worldwide. The actors leveraged CVE-2025-31324, an unauthenticated file upload vulnerability, to perform remote code execution.
Analysis from EclecticIQ links the intrusions to Chinese cyber-espionage units including UNC5221, UNC5174, and CL-STA-0048. The campaign focuses on compromising essential services and government entities across multiple countries, including the UK, US, and Saudi Arabia. The threat actors deployed malware including KrustyLoader, SNOWLIGHT, VShell RAT, and GOREVERSE to maintain persistent access and conduct espionage activities.
Reports indicate that the nation state actors had exploited the vulnerability weeks before the public announcement. The exploitation of widely used enterprise applications like SAP NetWeaver represents a strategic move to gain high-privilege access to internal networks and critical systems.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
LevelBlue Labs has created or updated the following Adversary Trackers to automatically identify and detect malicious infrastructure:
|
|
|
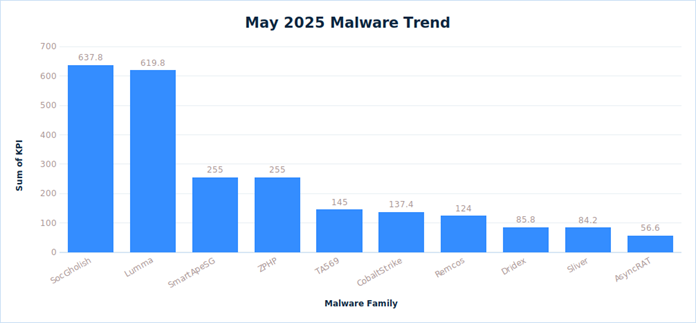
The team has identified the following malware/threat actors as the most active during the month of May.
|
- Lumma: Lumma activity continues to trend higher as more campaigns leverage the malware-as-a-service infostealer due to its modularity and ease-of-use. As popular IAB campaigns SocGholish and Clickfix continue to offer malicious actors convenient access to high value targets, Lumma’s will remain dominant for financially motivated threat actors looking to steal banking creds.
|
|
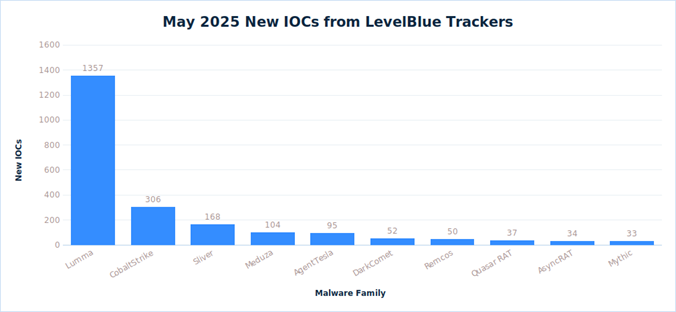
The LevelBlue trackers have identified over 2200 new IOCs for the different families it tracks. The busiest trackers during the month of May have been:
|
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In May, LevelBlue Labs added or updated 65 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- 6 new FortiAnalyzer detections.
- 4 Akamai detections including SQL injection activity, command injection, and IPS detections.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily.
LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise, IoCs, that are useful to members.
In May, 118 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|