|
|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
Scattered Spider Targeting Multiple Sectors
|
|
|
|
Scattered Spider has been active in 2025, expanding its targets from targeting fashion retailers to insurance providers, and more recently airlines and transportation companies. The latest breach was first announced by Hawaiian Airlines, but Erie Insurance, Aflac Insurance, and Philadelphia Insurance Companies all reported similar breaches the week of June 16th. As the decentralized group gains momentum and targets various sectors with smash-and-grab tactics, retail-forward companies should continue to bolster security measures and review any gaps in their security.
|
|
|
|
Iran’s Nobitex Exchange Breached
|
Nobitex, the largest Iranian crypto broker, was breached on June 18th and $90M of stolen funds were sent to inaccessible crypto wallets. The group claiming responsibility, Predatory Sparrow, had also breached Iran’s Sepah Bank a few days prior. As cyberattacks continue to operate in a gray zone, CISA and DHS have recently advised on proactive measures to harden defenses related to Iranian operations against US interests.
|
|
|
|
Salt Typhoon Breached Canadian Telecom via Cisco Flaw
|
Salt Typhoon had previously breached multiple US telecommunication companies, and have now claimed to have breached a Canadian telecommunication company. According to the Canadian Centre for Cyber Security, the breach occurred back in February. The group used a Cisco IOS XE vulnerability (CVE-2023-29198) to retrieve configuration files and modified one of the files to set up a GRE (Generic Router Encapsulation) tunnel for traffic monitoring. This move follows multiple investigations related to Salt Typhoon’s breach of US-based telecom companies, including Lumen, Verizon, and AT&T.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
The team has identified the following malware/threat actors as the most active during the month of June.
|
- SocGholish: Recaptures the #1 spot in June. SocGholish, also referred to as FakeUpdates, has been leveraged by multiple campaigns for initial access by tricking users into downloading an archived file with a malicious script inside. Given its modularity and ease of deployment, SocGholish remains a favorite method among threat actors and access brokers for staging.
|
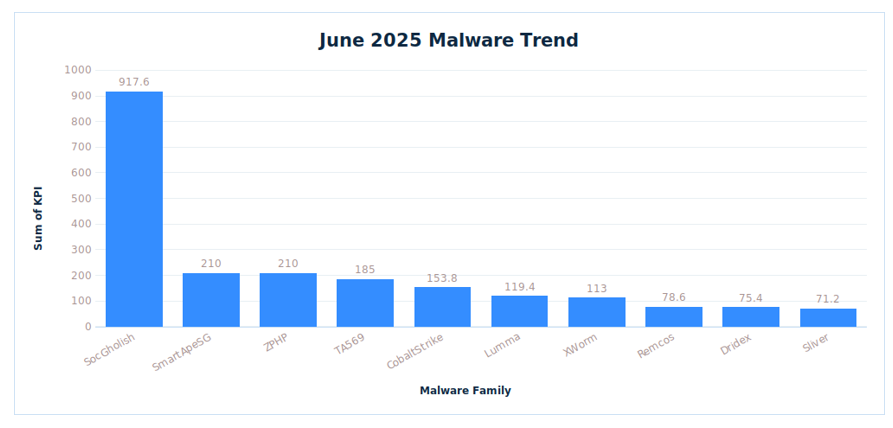
|
The LevelBlue trackers have identified over 1375 new IOCs for the different families it tracks. The busiest trackers during the month of June have been:
|
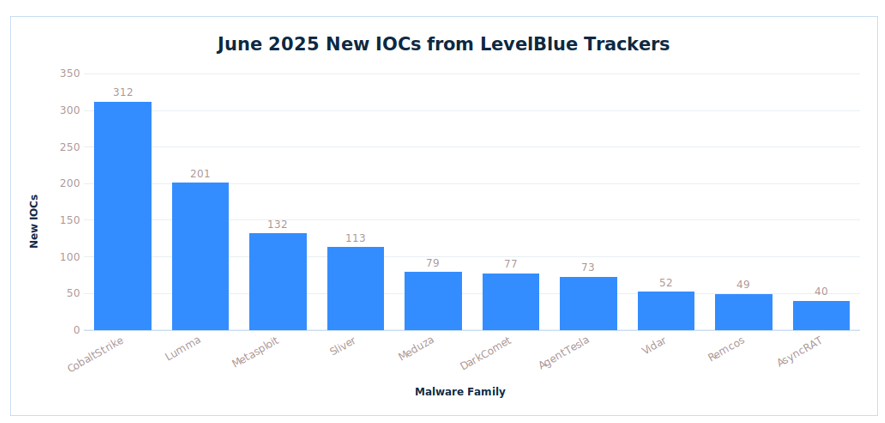
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In June, LevelBlue Labs added or updated 81 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- 7 new Cisco Advanced Malware Protection (AMP) detections.
- 3 new Kubernetes detections for service exposure, controller modifications, and Cron commands.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily.
LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise (IOCs) that are useful to members.
In June, 108 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|