|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
|
Latest Threat Intelligence News
|
|
|
|
|
|
|
Infected Cyberhaven Chrome Extension Distributed on Christmas
|
|
|
|
The attack occurred on Christmas, with the company removing the malicious package within an hour of detection. Users were vulnerable for over 30 hours, potentially exposing sensitive information.
|
|
|
|
Secret Blizzard Compromising Storm-0156 Infrastructure for Espionage
|
Since November 2022, Secret Blizzard has used Storm-0156's backdoors to deploy their own malware on compromised devices, particularly targeting government entities in Afghanistan and India.
The threat actor has employed various tools, including TinyTurla variant, TwoDash, Statuezy, and MiniPocket, alongside Storm-0156's CrimsonRAT and Wainscot backdoors.
The second part of the blog focuses on several other tools used by the APT. Between March and April 2024, Secret Blizzard utilized the Amadey bot malware associated with cybercriminal activity to deploy its custom Tavdig and KazuarV2 backdoors on Ukrainian military devices.
In January 2024, Secret Blizzard also leveraged a backdoor from Storm-1837, a Russia-based threat actor targeting Ukrainian drone pilots, to install its malware.
This activity highlights Secret Blizzard's tactic of leveraging other actors' infrastructure to diversify attack vectors and facilitate intelligence collection.
|
|
CVE-2024-49138, Vulnerability in Windows Common Log File System Driver (CLFS)
|
While details of in-the-wild exploitation are not yet available, it is noteworthy that ransomware operators have shown a growing tendency in recent years to exploit CLFS driver elevation of privilege vulnerabilities.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
The LevelBlue Labs team updated the following Adversary Trackers to automatically identify and detect malicious infrastructure:
|
- Meduza Stealer
- Lumma Info-Stealer
|
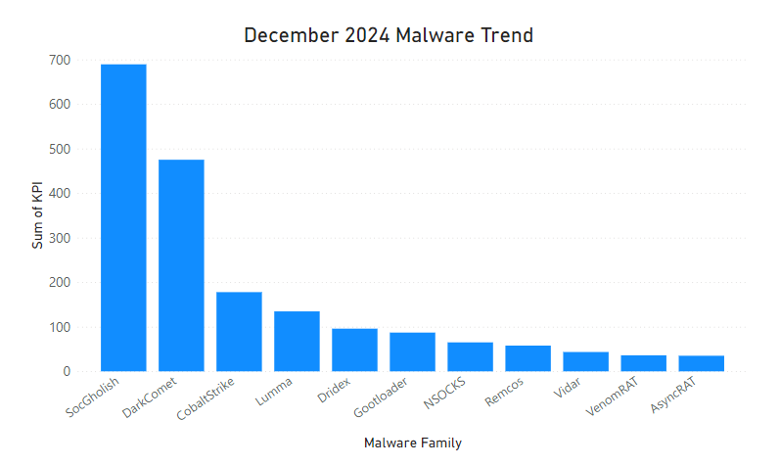
The team has identified the following malware/threat actors as the most active during the month of December. December’s malware trends continue to be very similar to previous months, with a main relevant inclusion:
|
- Lumma: The popular Info-Stealer continues to show up in the most popular malwares of the month, as well as on the list of most infrastructure detected in our Trackers.
|
|
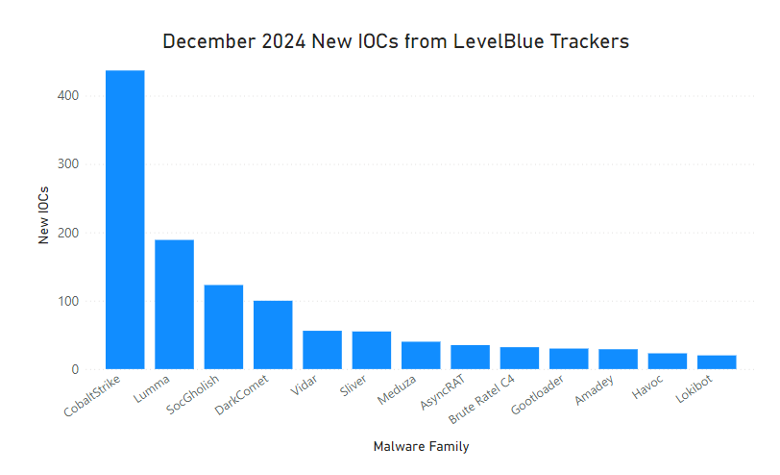
The LevelBlue trackers have identified over 1300 new IOCs for the different families it tracks. The busiest trackers during the month of December have been:
|
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In December, LevelBlue Labs added or updated 41 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- A new rule updating the approach to identify suspicious and potentially malicious files dropped by Office applications.
- New rules related to Brute Force Authentication and Password Spraying for Fortinet and Cisco Firepower.
- Several rules for Command and Control Communications and Malware detections by Trend Micro.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is the world’s largest open threat intelligence community, made up of 450K threat researchers who publish threat information from 140 different countries on the OTX platform, which our LevelBlue Labs team enriches and consumes. You can go here to find out more about the new pulses or to sign up to be part of the community.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise, IoCs, that are useful to members.
In December, 118 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|