|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
|
Latest Threat Intelligence News
|
|
|
|
|
|
|
Fortinet FortiOS Authentication Bypass CVE-2024-55591
|
|
|
|
LevelBlue Labs has released three correlation rules designed to address this vulnerability. Two of these rules focus on detecting suspicious login activities associated with CVE-2024-55591: 'Fortinet - Suspicious Login from Local Address IP (CVE-2024-55591)' and 'Fortinet - Automated Login-Logout (potential CVE-2024-55591)'. The third rule, 'Fortinet - Admin Added Via the Console', is specifically crafted to identify post-exploitation activity, such as the addition of new administrative accounts.
|
|
|
|
CVE-2025-23006: Actively Exploited SonicWall Vulnerability
|
CVE-2025-23006 is a critical deserialization of untrusted data vulnerability in the Appliance Management Console (AMC) and Central Management Console (CMC) of SonicWall SMA1000 devices. Exploitable by unauthenticated remote attackers via specially crafted requests, it allows arbitrary OS command execution under unspecified conditions.
|
|
RaccoonO365: The Latest Blog by LevelBlue Labs and the SOC
|
In September 2024, LevelBlue conducted a comprehensive threat hunt targeting artifacts indicative of Phishing-as-a-Service (PhaaS) activity across our monitored customer fleet. During the investigation, the LevelBlue Managed Detection and Response (MDR) Blue Team discovered a new PhaaS kit, now identified as RaccoonO365. The hunt confirmed true-positive compromises of Office 365 accounts, prompting swift customer notifications and guidance on remediation actions.
The initial findings were handed over to the LevelBlue Labs Threat Intelligence team, which further uncovered additional infrastructure and deconstructed the kit’s JavaScript. This analysis provided critical insights into the features and capabilities of the emerging PhaaS kit. Full details are in the latest version of the "Stories from the SOC" blog.
|
|
NEW: LevelBlue Threat Trends Report
|
We’re pleased to announce publication of the first LevelBlue Threat Trends Report! This biannual publication highlights threat activity observed by LevelBlue during the second half of 2024. Authored by the LevelBlue SOC in collaboration with LevelBlue Labs, it is a must-have for security practitioners at organizations of all sizes.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
The LevelBlue Labs team updated the following Adversary Trackers to automatically identify and detect malicious infrastructure:
|
|
|
The team has identified the following malware/threat actors as the most active during the month of January. This month’s malware trends continue to be very similar to previous months, with a main relevant change:
|
- Cobalt Strike: The adversary simulation tool has experienced a decline from its usual top 3 position this month, primarily due to two factors: it has been observed in fewer environments, and the number of automatically identified indicators by the Adversary Tracker has decreased.
However, this count of IOCs in the Tracker does not account for the numerous campaigns identified in the wild, which are added to manually created pulses.
|
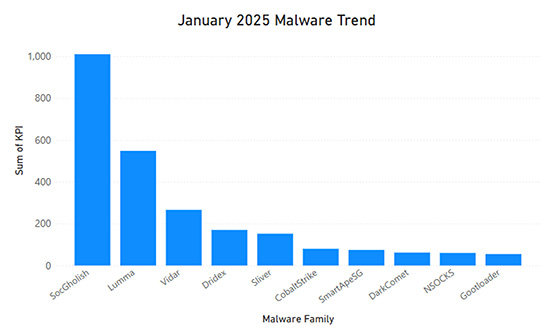
|
The LevelBlue trackers have identified almost 2700 new IOCs for the different families it tracks. The busiest trackers during the month of January have been:
|
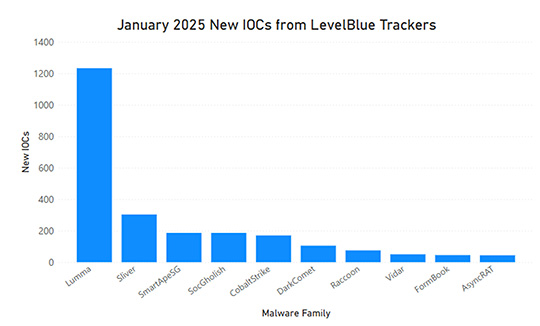
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In December, LevelBlue Labs added or updated 41 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- A new rule updating the approach to identify suspicious and potentially malicious files dropped by Office applications.
- New rules related to Brute Force Authentication and Password Spraying for Fortinet and Cisco Firepower.
- Several rules for Command and Control Communications and Malware detections by Trend Micro.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily. LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more. You can go here to find out more about the new pulses or to sign up to be part of the community.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more.
This includes indicators of compromise, IoCs, that are useful to members. In January, 104 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|