|
|
|
|
LevelBlue Labs
Threat Intelligence News
|
|
|
The LevelBlue Labs update gives you the latest threat news, including recent updates to USM Anywhere detections and new threat intelligence published in the LevelBlue Labs Open Threat Exchange (OTX), one of the largest open threat intelligence sharing communities in the world.
|
|
|
|
|
LevelBlue Threat Trends Report, 2025, Edition Two
|
|
|
|
LevelBlue has presented this week the second edition of our biannual Threat Trends Report, Fool Me Once: How Cybercriminals Are Mastering the Art of Deception. The report delves into threat actor activity observed in the first half of 2025 by the LevelBlue Managed Detection and Response (MDR) and LevelBlue Labs threat intelligence teams. In this report, our team offers in-depth analysis into the tactics utilized by attackers and provides recommendations on how to protect your environment.
Our research indicates social engineering is on the rise, now at 39% of observed initial access incidents and second only to business email compromise (BEC). Threat actors understand the simplest way into your environment is often the front door they were invited through by the end-user. Coupled with advancements in AI, attackers are quickly mastering the art of deception to gain an initial foothold and evade detection.
|
|
|
|
SharePoint ToolShell Vulnerability
|
The offensive security team from Code White GmbH was able to reproduce a chained bug recently presented at Pwn2Own Berlin. These bugs could end up as an unauthenticated RCE (Remote Code Execution) exploit chain in SharePoint, dubbed ToolShell. By using the ToolShell chain (CVE-2025-49706 + CVE-2025-49704), attackers can extract the ValidationKey and craft a signed __VIEWSTATE payload using a tool called ysoserial.
This payload allows the inclusion of any malicious commands and will be accepted as coming from a trusted input, achieving an unauthenticated RCE. Additionally, these cryptographic keys (ValidationKey and __VIEWSTATE) can be used to impersonate users or services even after the system has been patched, so persistence is gained in the system until the credentials are rotated in the system.
|
Microsoft Security Response Center (MSRC) issued an official advisory, now assigning the vulnerability identifier CVE-2025-53770 (a variant of CVE-2025-49704) and CVE-2025-53771 (a variant of CVE-2025-49706). On their page, Microsoft confirmed active exploitation in the wild and acknowledged the severity of the issue. On top of patching, Microsoft recommends rotating SharePoint Server ASP.NET machine keys to remove the persistence obtained in exploited systems.
In response to this news, LevelBlue Labs created several new Network Detections and Correlation Rules, which in conjunction with existing detections for suspicious webserver child processes, were able to detect exploited servers.
|
|
|
|
FileFix, A New ClickFix Variant
|
The ClickFix technique, which has gained popularity during this year among cybercriminals and state-sponsored actors alike, has been recently modified to elude the latest detections. Its latest version has been named FileFix by The DFIR Report in their most recent report 'KongTuke FileFix Leads to New Interlock RAT Variant.' This upgraded attack no longer relies on the terminal or Run dialog, but instead the File Explorer Address Bar. This alternative method was developed by mr.d0x, a security researcher and co-founder of a malware development academy. The method is described in one of their most recent blogs.
The report by DFIR analyzes the technique and attributes it to a recent campaign by KongTuke (aka LandUpdate808) delivering a PHP version of the Interlock RAT (Remote Access Trojan).
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
The team created the following Adversary Trackers to automatically identify and detect malicious infrastructure: Panda C2, Caldera C2, GoPhish, XMRig Monero Cryptominer, 7777 Botnet, ShadowPad, XtremeRAT Trojan, NanoCore RAT Trojan, Gh0st RAT Trojan, njRAT Trojan, Poison Ivy Trojan, Orcus RAT Trojan, Ares RAT C2, ZeroAccess Trojan, Hookbot, Hak5 Cloud C2, BlackNet Botnet, Pantegana C2, Supershell C2, Viper C2, NetBus Trojan, Unam Web Panel, BurpSuite, Mobile Security Framework (MobSF), Villain C2, RedGuard, SpiceRAT Trojan, Oyster C2, Mozi Botnet and Sectop RAT Trojan.
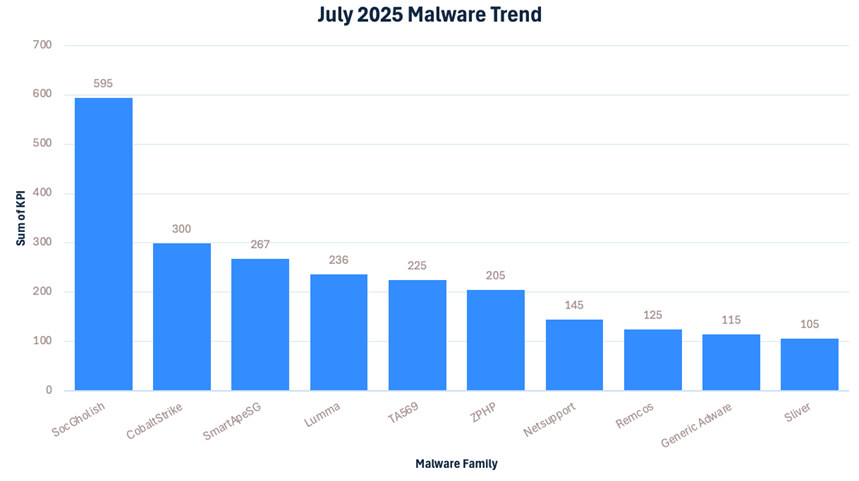
The team has identified the following malware/threat actors as the most active during the month of July. This month’s malware trends continue to be very similar to previous months, with one relevant inclusion:
|
|
|
|
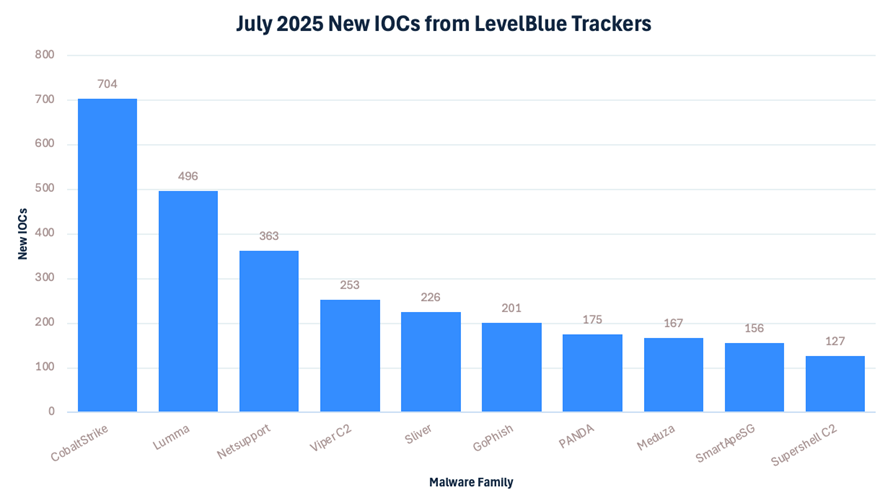
The LevelBlue trackers have identified over 4000 new IOCs for the different families it tracks. The busiest trackers during the month of July have been:
|
|
|
|
|
|
|
USM Anywhere Detection Improvements
|
|
|
|
|
|
In July, LevelBlue Labs added or updated 122 USM Anywhere detections. Here are a few examples of improvements and new elements LevelBlue Labs developed:
|
- New rules to alert on new and suspicious Salesforce administrative tasks.
- Several rule improvements on SentinelOne alerts.
- ToolShell exploit detection through a Correlation Rule and three new Suricatas.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
|
|
|
|
|
|
|
LevelBlue Labs Open Threat Exchange
|
|
|
|
|
LevelBlue Labs Open Threat Exchange (OTX) is among the world’s largest open threat intelligence sharing communities, made up of 450,000 threat researchers from 140 countries globally who publish threat information to the platform daily.
LevelBlue Labs validates, analyzes, and enriches this threat intelligence. Members of OTX benefit from the collective research, can contribute to the community, analyze threats, create public and private threat intelligence sharing groups, and more.
|
|
|
|
|
The LevelBlue Labs team is continuously publishing new pulses in OTX based on their research and discoveries. Pulses are interactive and researchable repositories of information about threats, threat actors, campaigns, and more. This includes indicators of compromise, IoCs, that are useful to members.
In July, 103 new pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new pulses:
|
|
|
|
|
|
|
|
|
|
|
|
LevelBlue Labs is the threat intelligence unit of LevelBlue and includes a global team of threat researchers and data scientists who, combined with proprietary technology in data analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as an organization’s attack surface expands, technology evolves, and adversaries change their tactics, techniques, and procedures.
|
|
|
|
|
|
|
|
|