|
|
|
|
Threat Intelligence Newsletter
|
|
|
|
|
|
Welcome to the August edition of the LevelBlue Labs Threat Intelligence newsletter!
LevelBlue Labs is the threat intelligence unit of LevelBlue. LevelBlue Labs includes a global team of threat researchers and data scientists who, combined with proprietary technology in analytics and machine learning (ML), analyze one of the largest and most diverse collections of threat data in the world.
Our research team delivers tactical threat intelligence that powers resilient threat detection and response — even as technology evolves, and adversaries change their tactics, techniques, and procedures.
In the Threat Intelligence Newsletter, you will find the most important threat news from the last month, recent updates to USM Anywhere detections, new pulses in OTX, and more.
|
|
|
|
|
|
Latest Threat Intelligence News
|
|
|
|
|
|
CrowdStrike incident and aftermath
The month has been marked by CrowdStrike's incident, where a faulty update on Falcon's Sensor caused the host's Microsoft Windows computers to crash, blocking their restart too. The events on July 19th caused downtime in approximately 8.5 million Windows systems, including major industries like airlines, banking, hospitality and healthcare, impacting the daily life of millions of people.
The incident was rapidly fixed, but it was seen as an opportunity for attackers, who have used it as a phishing lure in several campaigns started shortly after the incident. Dozens of new domains were created on the day of the incident, clearly trying to take advantage of the situation, delivering final payloads like RemCos or Lumma Info Stealer.
|
Cobalt Strike take down
Europol took down almost 600 Cobalt Strike servers used by cybercrime groups to control malware operations. Officials reported the takedown was the result of a three-year investigation that began in September 2021. Servers were identified and taken down with the help of multiple cybersecurity firms. According to security researcher Silas Cutler, the Europol operation appears to have taken down a quarter of known malicious Cobalt Strike servers.
|
AT&T breach
This month AT&T disclosed a breach occurred in mid-April, impacting phone call and message records of their clients. The company claims the incident occurred on a third-party cloud platform, meaning that it is likely related to the Snowflake hack that also impacted Santander Bank and Ticketmaster in June 2024.
|
OpenSSH vulnerability (CVE-2024-6387)
On July 1, 2024, Qualys published CVE-2024-6387, an unauthenticated Remote Code Execution vulnerability impacting the server component of OpenSSH (sshd). It was a known vulnerability patched since 2006, but the accidental removal of a critical component has resurfaced the vulnerability in versions since 2021 to July 1, 2024. The Proof of Concept was quickly available, but it depended on a race condition that was hard to achieve. The exploit takes more than 6 hours and over 10 thousand attempts to exploit a system, making it easier to detect and harder to exploit. Impacted versions went from 2021 to July 1st 2024, with only the 32 bit systems being vulnerable.
|
ServiceNow
On July 10, 2024, ServiceNow published several vulnerabilities, which may facilitate remote code execution, unauthorized access of sensitive data, and disruption of business operations. The security company Resecurity published a blog alerting of the available Proof of Concept (PoC) and attacks in the wild to exploit the chained vulnerabilities.
|
|
|
|
|
|
Tracking, Detection & Hunting Capabilities
|
|
|
|
|
|
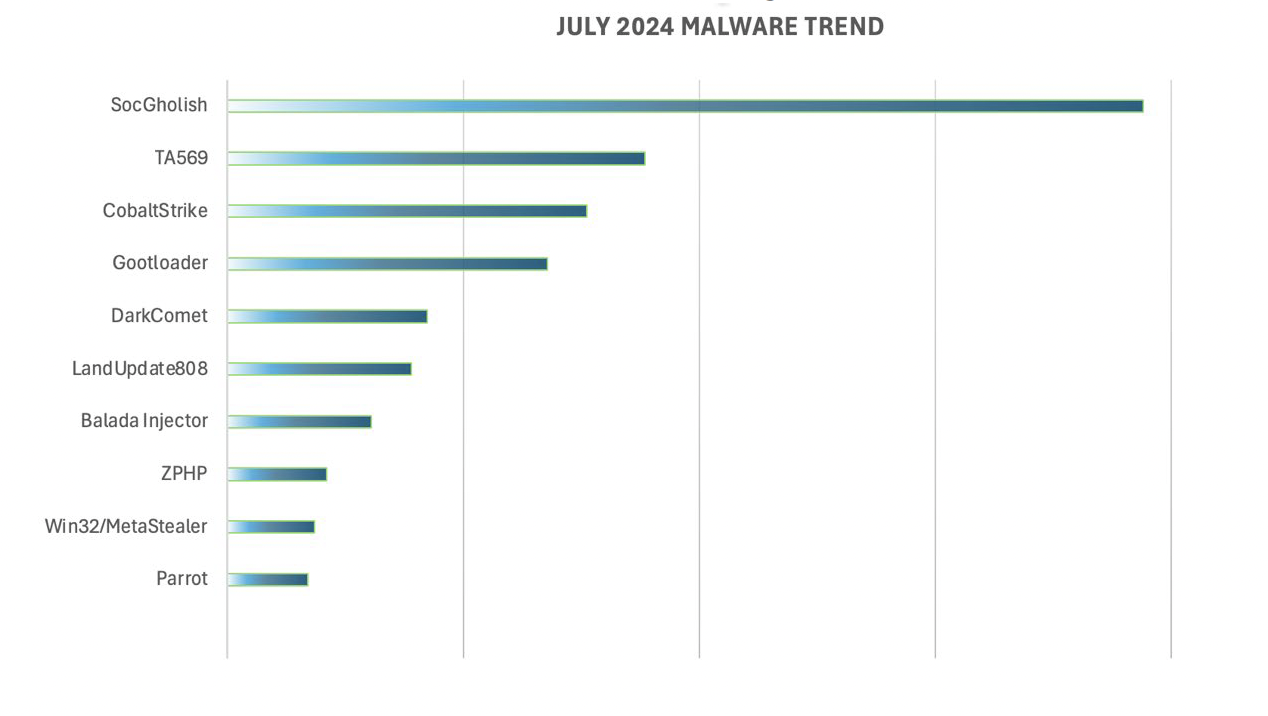
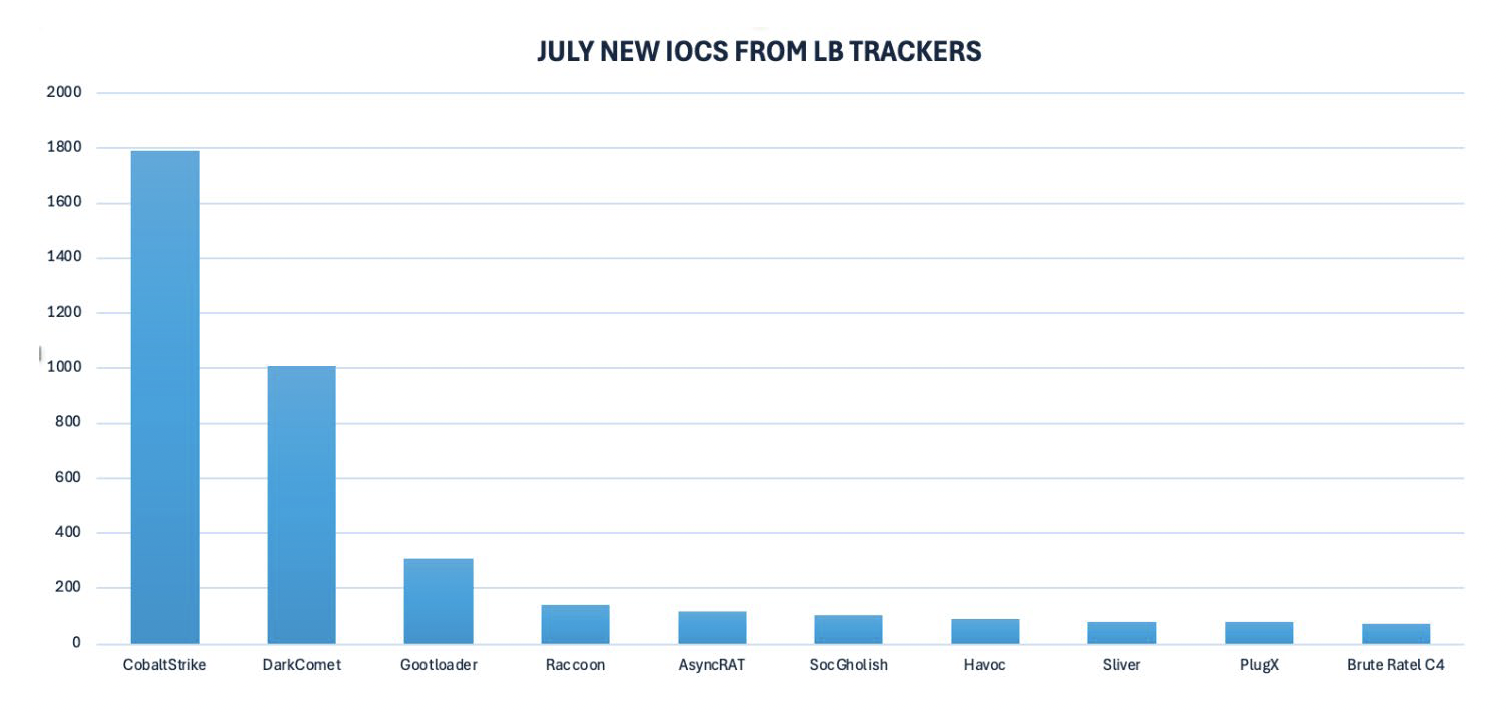
The team has identified the following malware/threat actors as the most active during the month of July. July’s malware trends continue to be very similar to previous months, with a few comments:
|
- SocGholish continues with the flow to be the most notorious malware family observed by LevelBlue Labs in June. The number of investigations created around it and the number of domains observed continue to significantly increase, while the rest of malware families have maintained similar numbers through last month.
- Cobalt Strike: LevelBlue Labs continues to observe similar statistics to its activity in the fleet when comparing it to last month’s behavior, despite Europol’s take down at the beginning of the month. The number of new IOCs associated with Cobalt Strike’s infrastructure identified by LevelBlue’s tracker is almost identical to June’s results, so the threat actors behind the taken down infrastructure have not urged to replace their infrastructure.
|
|
|
USM Anywhere Detection Improvements
In July, 50 USM Anywhere detections were added or improved. Here are a few examples of improvements and new elements created:
|
- Created new Network detections to identify ServiceNow exploit attempts to CVE-2024-5178 and CVE-2024-5217.
- Created several new rules related to Anomalous User Behavior for Okta, anomalous activity after phishing emails and other generic anomalities.
- Enhanced AWS rules for suspicious network Access Control modifications, specifically looking at AWS EC2 Security Groups.
- Improved Microsoft Defender for Endpoint rules to enhance the response by event severity.
|
Please visit the LevelBlue Success Center for a full list of improvements, new elements, issues found, and tasks created.
|
LevelBlue Labs Open Threat Exchange
LevelBlue Labs Open Threat Exchange (OTX) is the world’s largest open threat intelligence community, made up of 450K threat researchers who publish threat information from 140 different countries on the OTX platform, which our LevelBlue Labs team enriches and consumes.
You can go here to find out more about the new pulses or to sign up to be part of the community.
|
New OTX Pulses
The LevelBlue Labs team is continuously creating new Pulses in OTX based on what they are seeing in the wild. In July, 102 new Pulses were created by the Labs team, providing coverage for the latest threats and campaigns. Here are a few examples of the most relevant new Pulses:
|
- Ticket Heist: Olympic Games and Sporting Events at Risk
- Scam Attacks Taking Advantage of the Popularity of the Generative AI Wave
- FIN7 Reboot | Cybercrime Gang Enhances Ops with New EDR Bypasses and Automated Attacks
- Likely eCrime Actor Capitalizing on Falcon Sensor Issues
- Malware Distributed Using Falcon Sensor Update Phishing Lure
- LummaC2 Malware Abusing the Game Platform 'Steam'
|
|
|
|
|
|
To have Release Notes emailed to you automatically, follow these steps:
|
2. Click on the announcement for the product you wish to follow.
3. Select the “Follow” button on the right-hand side.
4. Select the drop-down menu on the right-hand side and choose “Every Post” to enable receiving emails from leading security and IT tools.
|
|
|
|
|